
Karroubi in Danger and Other Stories
August 29, 2011
Man in Middle Attacks Dangerous in Iran – Part 2
September 2, 2011
It all began with a simple message. An Iranian internet user was trying to connect to Google using the Chrome browser. Strangely enough, his browser flashed a message telling him that the security certificate he was using to access Google was not theirs. The user went to Google’s help forums to follow up on this and an investigation followed which uncovered a secretive, but highly explosive plot: a security firm in the Netherlands, DigiNotar, had seemingly provided a certificate to “someone” in Iran that allowed access to all secure traffic over Google within Iran.
People in Iran connecting to Google had their traffic diverted. It has always been possible to divert internet traffic sent over unsecured lines (http:// instead of https://). Diverting secure traffic without anyone noticing required access to a security certificate. Because someone in Iran had managed to get security certificate in Google’s name, it took nearly two months for the breach to be discovered.
There are two ways this certificate could have been obtained. Someone could have contacted the DigiNotar sales team and purchased it by simply impersonating a Google employee. Or their site was hacked and the certificate was forged. Either way points to a breach of security at the company. If it was sold to someone other than a Google representative it means that there were not enough procedures in place to verify the identity of requestors. If the site had been hacked, DigiNotar has serious issues with their internet infrastructure.
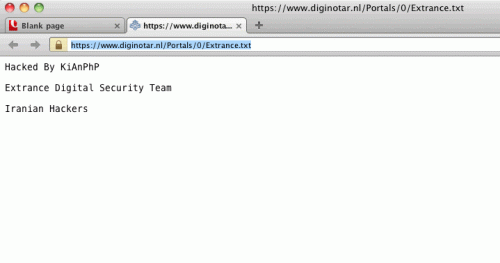
Security bloggers are reporting that the site may have been hacked earlier, in 2009. Screenshots of hacked pages are being shared via the internet. The links to those pages were available as recently as the morning (in Europe) of August 30th.
These types of security breaches are known as Man in the Middle (MITM). When secured information is sent over the internet both parties, the sender and the requestor, have the keys necessary to send the message safely. So, as the sender, you have one piece of information that authenitcates your identity and the identity of the receiver. The receiver also has a piece of information that tells the sender, “Yes, I am who you think I am.” In order to divert this, a “man in the middle” must have a way of appearing as both the receiver and the sender. As such, he can change the messages from either party. Here’s an example of MITM in a real world sense:
Suppose you want to send mail to your brother. But an enemy somehow manages to get credentials of a postman and bribes or coerces his way into becoming the postman that takes your mail to your brother and brings his reply back. Now when you put mail in the mailbox, he will discard your mail and instead, write a mail himself and take that to your brother as if you had written it. Then, when your brother writes a reply to your mail, the postman picks that one up, discards it and writes a totally different reply and brings it back to you.
The result is that neither you nor your brother are able to communicate what you wish to communicate to each other if the enemy wishes to alter your message. Worse, even if he doesn’t, any secret that you sent, including your addresses and passwords are now the property of the enemy. Now imagine the government of Iran or another government being that postman, reading every message you send over Google…
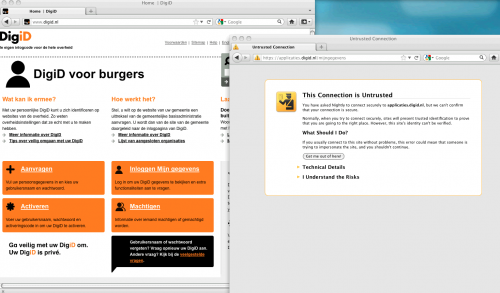
In order to stop such attacks, Firefox and Chrome are already working on browser updates that do not accept DigiNotar security certificates. This is of special concern in the Netherlands because the Dutch government uses DigiNotar for secure government-citizen transactions.
Man-in-the-Middle attacks have been used by Iran and Syria, among others, in the past to gain access to secure data. Earlier this year the security certificate firm Comodo, also released nine fraudulent security certificates, many of which ended up in Iran.
However, the absolute worst part of all of this is that this has been going for two months. There really is no telling how many people have been targeted inside Iran and how many are about to be targeted. If you live inside Iran, the first thing you can do is download the latest version of Google Chrome or Mozilla Firefox. It’s always a good idea to use Tor or other encryption methods to secure your connection. Using Tor, however, does not guarantee that you will be safe from Man in the Middle Attacks.
Furthermore, use Google’s 2-step verification. Here’s how from Google’s own website with a pictorial guide.
Arseh Sevom is concerned about this and is monitoring the situation closely. We will be updating on this situation regularly and providing our readers with more information. Please subscribe to our feed for regular updates.
Links to more information:
Response from DigiNotar’s parent company, Vasco
The Guardian reports on the MITM attack
Google states that the attack focussed on users in Iran
Some speculation on scenarios involving falsely obtained certificates from ComputerWorld
Early response from Mozilla to news that security was compromised
Microsoft Security Advisory
Electronic Frontier Foundation on the vulnerability of Certificate Authorities
Concern in the Netherlands over the security of the Dutch company that provided the certificate (in Dutch)
This post is part of special series of articles focusing on managing your online security and privacy. The complete series can be found in Persian at this link: http://bit.ly/n19Pzk. If you have questions about the internet, privacy, or online security, you can ask our security editor using the form on the website or by emailing: [email protected].




