
Man in the Middle: Google Becomes Dangerous in Iran
August 30, 2011
Protests in Iran spurred by Disappearing Lake
September 5, 2011
UPDATE: Google and Mozilla have revoked more than 200 security certificates as a result of a hack into the accounts of certificate authority, DigiNotar.
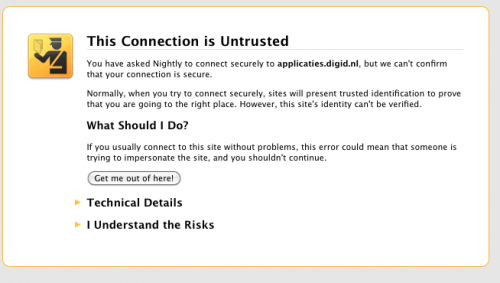
WARNING: Tor, Yahoo, and Mozilla were among the targets.
WHAT THIS MEANS: If you are in using Tor software downloaded after July 9, it might be compromised. Users of confirmed versions of Tor should not have been effected. (Read more on the Tor Blog.) If you have not checked the signature of Tor to ensure that it is authentic, now is the time to do so. Instructions are here.
MORE THAN 200 SECURITY CERTIFICATES STOLEN
A few days ago, Arseh Sevom reported on compromised security for users in Iran. It was reported that a security certificate was stolen and was in used in Iran. This certificate was used to access secure communication between users in Iran and Google.
Now it has been revealed that over 200 hacked certificates are in use. Chrome and Firefox have revoked those certificates meaning that those using the most recent versions of those browsers should see warning messages if they try to access a site using a stolen certificate.
A hack-free site or application is the holy grail of internet security. As long as the data is compelling enough, the challenge great enough, and snooping technology advanced enough, there will be hackers who find their way in. This is what happened to the Dutch security company DigiNotar when hackers in Iran made their way into the site sometime around July 10, 2011. DigiNotar provided secured connections to the Dutch government and others.
On July 19th, DigiNotar discovered the hack. They believed they had tracked down and destroyed all of the stolen security certificates. It now appears that over 200 certificates were stolen. Some of the sites that could have been compromised include Tor, Mozilla, and Yahoo. The false certificate that spurred the investigation was issued in the name of Google.
A BLANK CHECK
The certificate in the name of Google was used by several Internet Service Providers (ISPs) in Iran, suggesting that whoever hacked DigiNotar was affiliated with the government or a powerful organization. Some of the secure communication between Google account users in Iran and Google was circumvented to a server where it could be, at the very least, observed. “If you have control over all ISPs, then it’s easy to reroute traffic to a proxy server,” says Hans Van de Looy, principal security consultant and founder of the Dutch security company Madison Gurkha. “If you don’t have control it’s a bit harder.” Van de Looy continues:
“This is a complex and elaborate hack. If it is true that more than 200 certificates were stolen, and we think it is, the hackers had access to the root key.”
In a sense, this access was like a signed blank check for the hackers. They could use it to impersonate an implicitly trusted source and divert information thought to be secure.
DETECTED BY USERS OF GOOGLE CHROME
The certificate for Google was not in constant use, which meant that it took longer to detect. It was detected by users of Google Chrome. The browser detected that the certificate being used was not one owned by Google because the company’s security certificates were hard-coded into the browser.
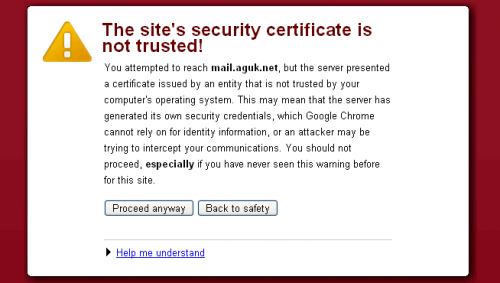
CERTIFICATE AUTHORITIES
DigiNotar and its parent company Vasco are among a few dozen companies known as a Certificate Authorities. Certificate Authorities essentially assure that a party, such as Google, is who they say they are. This is important when sensitive information is sent over the internet.
Just as an ID can be forged or stolen, so can a digital certificate. When this happens, every user who connects to a site over a connection that uses a stolen certificate is vulnerable. At the very least, their secure activities — for instance, logins — can be observed.
Some security experts are asking how we can protect our information using a system as vulnerable and prone to hacks as the current one? Right now, there is one guard at the door. That guard can be bribed, compromised, blackmailed, circumvented, or asleep on the job. Distributed responsibility for security could add a few more layers of protection. In a sense, this is what happened with the stolen certificate in the case of Iran when Google’s own browser detected the forged certificate. (The browser acted as an extra guard. Google Chrome developers are offering this opportunity to all owners of secure sites. They can have their security certificates hard-coded into the browser architecture.)
The Electronic Frontier Foundation warns of the vulnerability of the current system of guaranteeing security:
The certificate authority system was created decades ago in an era when the biggest on-line security concern was thought to be protecting users from having their credit card numbers intercepted by petty criminals. Today Internet users rely on this system to protect their privacy against nation-states. We doubt it can bear this burden.
For more information:
The Electronic Frontier Foundation’s report on security issues.





